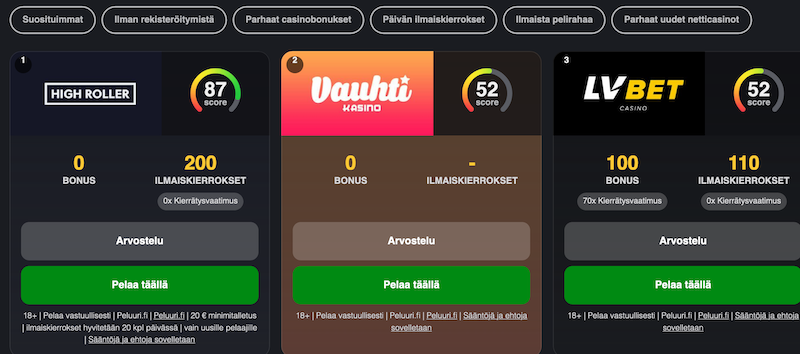
Back in 2008, Trustly launched the groundbreaking concept of Pay N Play, or in other words – Trustly Casinos. This service is currently available to players from Germany, Sweden, Finland, Estonia, and the Netherlands. What makes Pay N Play so special is the ultimate convenience it offers to players.
It lets you leave behind all the boring and lengthy verification procedures. In return, fans of online casinos get to focus on the action solely. All this, moreover, is 100% safe and secure. Pay N Play Trustly casinos won’t ask for your ID or any other documents. The platform does all the verification processes in the background. You simply log in, deposit, and play. It’s as simple as that. Take a look at the review to the most popular casinos.
How BankID and Pay N Play Work?
The genius behind Pay N Play is the BankID feature, in fact. This is an electronic ID system that connects a network of established European banks. Thanks to this service, Trustly gets to verify your identity in the background using the ID, bank statement, utility bill, or anything else. This saves you precious time and lets you enjoy the casino games rather than bothering with documents.
Getting Started with BankID Casinos
Only players from selected European countries can use this service. If you live in one of those (Germany, Finland, Netherlands, Sweden, and Estonia), getting started is a breeze. There’s nothing special you need to do. Quite on the contrary, the process is as it follows:
- Visit any of the Pay N Play casinos listed here.
- Select the option to make a Trustly deposit.
- Complete the payment process.
- Start playing as the system does everything else in the background.
As you can see above, you don’t even have to complete a registration process. Suppose you wonder what happens with your funds, there’s no need to worry. The system is smart and recognizes you the next time you play, so your funds are there. If you don’t decide to cash them out, that is.
Features of Trustly Pay N Pay Casino Sites
To understand what makes any Pay N Play casino special and attractive, you must discover its best features first. So, let’s see what the main benefits of playing at no verification gambling sites are.
- 100% safe – There’s no need to worry about anything when playing at no ID gambling sites. They employ the latest safety standards. BankID itself is a secure system used by leading banks in Europe. So, all your details are safe.
- Convenient – Imagine making your first withdrawal and then having to bother with the KYC process. It’s frustrating and time-consuming, we know. Well, instant play casinos that use Trustly don’t have this procedure at all. Meaning, they’re as convenient as it gets.
- Instant deposits and withdrawals – Waiting for days for your online casino payment and withdrawal to complete are in the past. Trustly transactions are instantly processed. That’s right. Your deposit and cashout arrive within seconds. This is actually one of the vital pros of playing with Pay N Play gambling websites.
- Mobile play supported – Pay N Play is a service of the future. As such, it makes sense that it works perfectly on all types of devices. It is mobile-ready and available at reputable mobile casino sites. This means that you can take your favourite casino games everywhere with you. You get to make instant deposits and cashouts without completing a KYC process too.
Bonuses at Pay N Play Casino Sites
Casino bonuses are an essential part of the iGaming adventure. They let you boost your bankroll and play longer. As such, they are also highly desired by players. One particularly popular type of casino bonus is the welcome offer. Operators usually give the welcome bonus alongside your first deposit and upon registration. As there’s no registration at no account gambling sites, it makes sense that consumers are worried about their bonus opportunities.
There’s no need to worry! While Pay N Play iGaming sites usually have no sign-up bonuses, they have lots of other promotions. So, you get to claim deposit bonuses, free spins, playing chips, and more. Again, VIP rewards aren’t an option at most websites. However, BankID casinos make sure to make up for this with other promos, tournaments, and bonuses.
Does Using Trustly Cost More?
Nobody wants to pay extra fees when making casino deposits or requesting withdrawals. That’s why Trustly is so awesome. Using its Pay N Play service doesn’t cost more. In fact, it costs nothing. There are no additional processing fees associated with using Trustly. That can’t be said, for example, for bank transfers and even credit card billing. Meaning, you get instant transactions without paying extra. It doesn’t get any better, really.
Are BankID Online Casinos Legit?
Yes, absolutely. Trustly only works with regulated and licensed online casino operators. Meaning, they have high operating standards. These include licenses from leading authorities such as the MGA and the Swedish Gambling Authority. Moreover, Pay N Play casinos are often approved by independent auditors, too. So, don’t be surprised to find seals of approval from eCOGRA, TST Labs, iTech Labs, and so on.
Pay N Play Casino Games
Registering with BankID casino sites doesn’t mean that you sacrifice playing your favourite casino games. Quite on the contrary. The game selection at these gambling sites is impressive and powered by leading developers. That’s right. Trustly is accepted at popular casino operators that feature games by NetEnt, Microgaming, Play’n GO, Betsoft, and more.
Are you wondering what types of casino games are available at Trusty casinos? Well, let’s go over them together.
- Online slots – You can find all the fan-favourite slot machines at BankID casino sites. These include top picks like Immortal Romance, Under the Bed, and Gonzo’s Quest. The slots menu really depends on the software the casino uses and has no relation to the Trustly system. Only legalised slots on bedstecasino.org.
- Table games – Fans of table games get to enjoy lots of variations of roulette, blackjack, baccarat, and poker. Depending on the game suppliers, there may also be options like sic bo, craps, and so on.
- Speciality games – Keno, online bingo, and scratch cards are some of the speciality games found at Pay N Play Trustly casinos. Again, the exact offer depends on the game developers that supply the specific casino site.
- Progressive jackpots – Hitting a massive progressive jackpot is entirely possible at Pay N Play gambling sites. As these operators work with providers like Microgaming and NetEnt, you can expect their best titles. Yes, we refer to Mega Moolah, Mega Fortune, Hall of Gods, and the rest.
- Live dealer tables – Live dealer casinos are increasingly popular these days. Well, good news to all those players who love live casino actions – it’s available at Pay N Play casinos too.
Easy Branches Global Guest Posting Services in multi languages
Best last minute News headlines from Your Country and inborn language
Yachts News | Discover the Exclusive World of Yachts
Yachts Listings for Sale and Charter
immediate for delivery New Exclusive Hyper, Mega, Classic and Super sports Cars